Secrets Management
SyncBackPro can be used with popular secrets managers to retrieve usernames, passwords and private keys. This removes the need to store encrypted passwords in the settings and allows for all the benefits of using a secrets manager, e.g. auditing, password rotation, etc.
The following secrets managers are supported:
•AWS Secrets Manager
•Azure Key Vault
•Google Cloud Secret Manager
•Windows Credential Manager (local, part of Windows)
•HashiCorp Vault (open source)
SyncBackPro only requires read access to the secrets manager (list the secrets and retrieve the value of a secret). It does not create, delete or modify secrets stored in a secrets manager. Also, the value stored for a secret is never shown to the end user nor stored locally. The remote secret must be in plain text or JSON format.
Connecting to a Secrets Manager
To use a secret you must first create a connection to a secrets manager. Multiple secrets can share the same connection. To create a connection:
•Go to the Secrets Manager (via the main burger menu ![]() )
)
•Go to the Connections page
•Click the Create button and choose the appropriate secrets manager from the pop-up menu, e.g. Amazon:
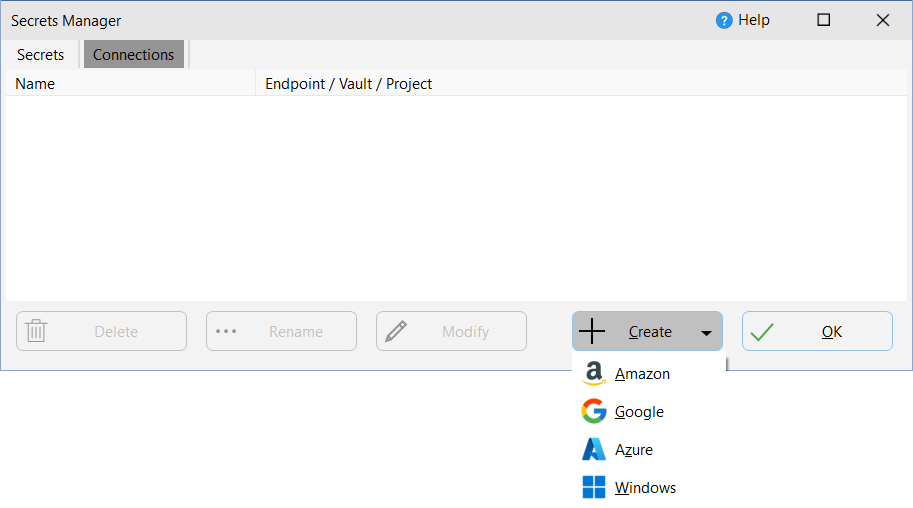
You are then prompted for the connection details based on the type of secrets manager:
Name: The name you want to give to the connection. This is for your reference.
If you are using Amazon AWS Secrets Manager:
Access Key ID: Your access key ID.
Secret Access Key: Your secret access key.
Endpoint: Choose the region (endpoint) that the secrets manager is physically located.
If you are using Google Cloud Secret Manager:
Please select your Service Account Private Key file (JSON): A JSON private key file is required.
If you are using Microsoft Azure Key Vault:
Vault: The vault ID.
If you are using HashiCorp Vault:
Vault Token: The vault login token.
URL: The URL of your HashiCorp vault service. This is typically in the form of http://hostname:8200/v1/secrets_engine/. You may get a 404 error if there are no secrets.
If you are using the Windows Credential Manager then only a name is required.
Once a connection has been established to your secrets manager you can define what secrets you want to use. You can define as many connections as you need. Multiple secrets can use the same connection.
You can Delete, Rename and Modify your existing connections. Note that a connection cannot be deleted if it is being used by a secret (see the Connection column on the Secrets tab).
Define Secrets
Once you have defined at least one secrets manager connection you can specify which secrets you want to use that are stored in that secrets manager. To to this:
•Go to the Secrets Manager (via the main burger menu ![]() )
)
•Go to the Secrets page
•Click the Create button and choose the type of secret you wish to use. There are three types of secrets:
•Usernames
•Passwords (including SSE-C cloud encryption keys)
•Private Keys (for SFTP)
You are then prompted for the secrets details:
Name: SyncBackPro will retrieve a list of the names of all secrets defined in your secrets manager. You must select the secret you wish to use.
Description: If the secrets manager has a description of the secret then it is retrieved. The description is for your reference only (the description in the secrets manager is not changed).
Key Name: If the secret is stored in JSON, or as key/value pairs, then you must choose which key to retrieve the secret from. For example, a secret may contain both a username and a password, so you must choose which key stores the appropriate value.
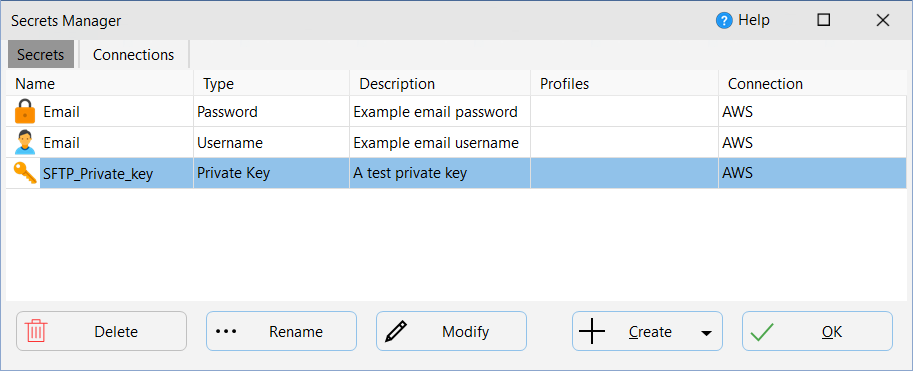
To delete a secret, click the Delete button. You cannot delete secrets that are being used by a profile (see the Profiles column to see which profiles are using a secret). Note that deleting a secret does not delete it from your secrets manager.
To change the description of a secret, click the Rename button. A secrets name is set in your secrets manager so it cannot be changed.
To modify a secrets definition, click the Modify button or double-click a secret.
Using Secrets
Secrets can be used in several settings for a profile:
oFTP/SFTP username and/or password
oSFTP private key password and/or SFTP private key
oEmail username and/or password
oCompression password
oThe password for the log file sent via email
oBackup email username and/or password
oNetwork username and/or password
oCloud username and/or password
Using a secret is simple. In the New Profile Wizard, or when modifying an existing profile, if a secret can be used then you can select it from the drop-down menu. For example, with SFTP you can choose to use a secret for the SFTP private key:
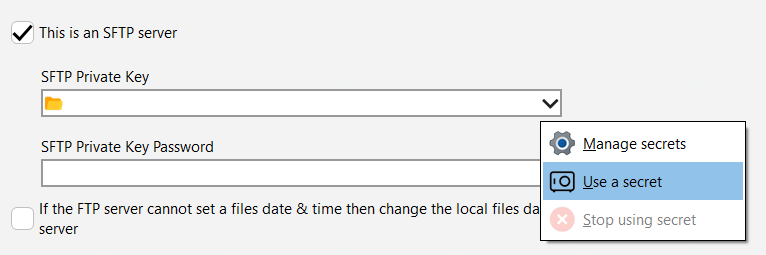
When you select Use a secret you can then choose the appropriate secret. From the pop-up menu you can also create new secrets (via Manage secrets) and also select to stop using a secret.
If a secret is being used you'll be able to see which via the hint on the drop-down menu button and also in the pop-up menu, for example:
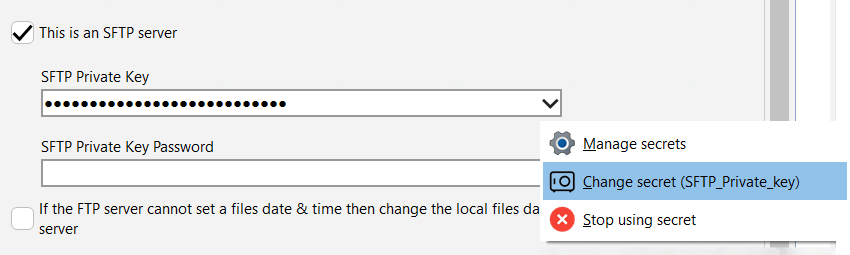
The value of a secret is never stored locally nor shown to the user (this includes usernames). Within the profiles settings, a secret is similar to a variable, but is hidden from the user.
What is Secrets Management?
Secrets management is the process of securely storing and managing sensitive information, such as passwords, authentication tokens, and encryption keys.
A secrets manager and a password manager are both tools used for managing sensitive information, but they serve different purposes and have different capabilities.
A password manager is a tool used for securely storing and managing passwords. It allows users to generate and store complex passwords for different accounts, reducing the risk of password reuse and making it easier to maintain strong passwords. Password managers often include features like password strength analysis, automatic password filling, and password synchronization across multiple devices.
A secrets manager is a tool used for securely storing and managing any type of sensitive information, not just passwords. This can include API keys, encryption keys, tokens, and other types of credentials. Secrets managers often provide more granular access controls and audit trails to help manage secrets across an organization.
Typically an end user would use a password manager, e.g. LastPass, to login to web sites and services. In most cases only a single user has access to the passwords stored in a password manager. Password managers require that the user manually authenticate themselves first, e.g. they must manually enter a password. A secrets manager is usually used by software, such as SyncBackPro, and not end users. The secrets are stored online using a cloud service, e.g. using AWS Secrets Manager, and can be accessed and used by multiple users (people or software). Secrets managers often audit access to the secrets and limit what secrets a user can access.
Where are Secrets Stored?
The connection information (to the secrets managers), and which secrets to use, are stored in the program settings (like shared settings are). This means when exporting a profile, the importer of the profile will not have access to the secret.
The value of secrets, e.g. actual passwords, are never stored locally nor shown to the user.
Windows Credential Manager Limits
The Windows Credential Manager user interface has a limit of approximately 512 characters for the maximum username length, and 259 characters for the maximum password length. This is a bug within that software as the actual maximum password length should be approximately 1,280 characters (2,560 bytes). It is possible to get around this limit using PowerShell, for example.
For limits with other credentials managers, e.g. HashiCorp Vault, refer to their documentation.
All Content: 2BrightSparks Pte Ltd © 2003-2025